In 1905, philosopher George Santayana famously wrote that “those who cannot remember the past are condemned to repeat it”. He claimed that when experience is not retained, what remains is a perpetual infancy. Discussions about the internet suffer from this too, despite its young age. Could it be that the hot topics of today are as old as the internet itself? Diving into archives such as Textfiles.com and WWWTXT gives us an answer.
The joy of handles
“May we ask dear Captain Kirk that it would be very polite if you could use your real name?” Captain Kirk was participating in online discussions in which the vast majority of people were using their real name. It was a polite request. It is a request Facebook makes of all its users: “Facebook is a community where everyone uses the name they go by in everyday life. Always knowing who you’re connecting with helps keep you and the rest of our community safe from impersonation, scams and phishing.”
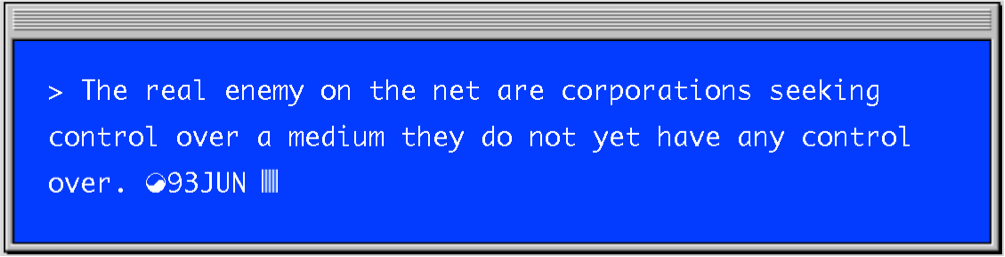
But the request to Captain Kirk was made long before the Facebook-era. It was made in 1992, some 12 years before Facebook was launched and one year before the World Wide Web even existed. And just as Facebook’s policy did over a decade later, it sparked an intense debate over whether or not such requests could and should be made of users.
In response to the request, made by a moderator of the Boston Computer Society, Mahatma Kane Jeeves (a pseudonym) and David Lescohier (not a pseudonym) wrote a long post titled “The Joy of Handles”. Their post ominously opens with “Do you trust me? If you participate in computer conferencing, and you use your real name, then you’d better.” What follows is a long outline of why using your real name online is sometimes a Very Bad Idea, a sentiment echoed years later by vulnerable minorities during the discussions surrounding Facebook’s real-name policy. But what the post perhaps does best is explain that although the medium is new, communicating anonymously is far from it. It explains that we communicate anonymously every day and, in many cases, with good reason. From anonymous callers who vent their opinions on talk radio shows, to celebrities using stage names. However, the authors ponder, do ordinary computer users need the same type of protection? If you think they don’t, consider the scenario the authors offer:
“One day you are nominated to the Supreme Court. Who are all these strange people on TV claiming to be your friends? How did that fellow know your position on abortion? Your taste in GIFs?”
Some twenty-five years before we’d witness the first flood of people being fired over old Twitter posts, “The Joy of Handles” had warned us that exactly this might happen.
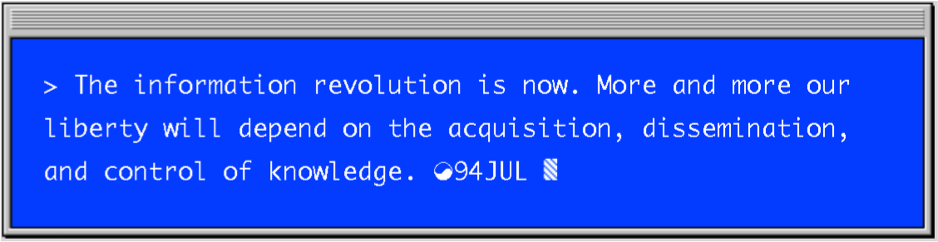
Private communications as munitions
The authors’ prescience doesn’t stop there. They go on to warn us that while mail correspondence and telephone traffic had, up to then, been hard to monitor due to the work involved in opening envelopes and tapping wires, this was about to change. “[In] the medium of computer communications, most surveillance can be conducted using automated monitoring techniques. Tools currently available make it possible and even cost-effective for government and other interests to monitor virtually everything which happens here.”
Something had to be invented by these early internet users to keep private information private. And something was. The early nineties saw the first distribution of publicly available encryption software. Today, encryption secures our online communication, from online banking to our WhatsApp messages. But when the first encryption software was released, it was classified by the US government as munitions, to be regulated for national security purposes with intensive export restrictions. The now famous cryptographer Daniel Bernstein, then a PhD student at Berkeley, sued the US government, challenging these restrictions and arguing that source code should be protected under the First Amendment. The digital rights organization Electronic Frontier Foundation supported him and together they managed to get the following ruling:
“This court can find no meaningful difference between computer language, particularly high-level languages as defined above, and German or French….Like music and mathematical equations, computer language is just that, language, and it communicates information either to a computer or to those who can read it…” – Judge Patel, April 15, 1996
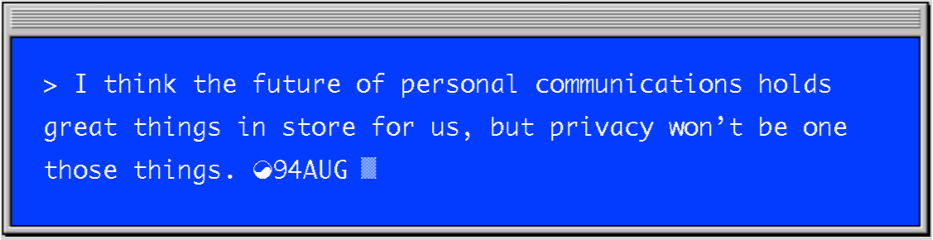
It was a landmark case that led to the free distribution of encryption technology that to this day allows dissidents from dictatorial regimes to communicate freely with newsrooms in democratic states. It allows communities at risk to have online discussions without needing to fear repercussions. It allows for more secure systems, networks and data storage. It was exactly what the internet needed to grow into a more safe and mature network, paving the road for the secure communications and e-commerce we all enjoy today.
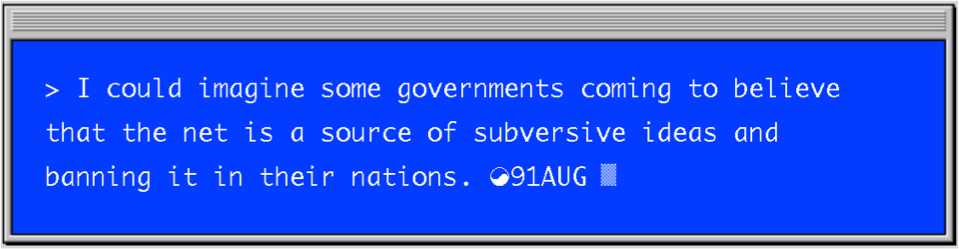
Trying to label encryption as “munitions” wasn’t the government’s only tactic to stop people from using it. In 1993, the National Security Agency released the Clipper Chip, an encryption chip that was intended to be adopted by the telecommunications industry, with a secret backdoor that meant the NSA could monitor the encrypted communications provided by the chip. Unsurprisingly, no customers and thus no telecommunication providers were interested in it.
The use of encryption is, to this day, hotly debated. When WhatsApp enabled encryption by default, thereby securing messages sent via their app, intelligence agencies and police around the world cried foul. How were they supposed to monitor people’s private conversations now? And politicians continue to ask for backdoors in encryption so that court-ordered interception can take place. The grievances cryptographers had back then against backdoors in encryption protocols are no different than the grievances of cryptographers today, yet the discussion resurfaces with every new government cycle.
From local bazaars to global shopping malls
While the same discussions around anonymity, encryption and privacy continue to resurface, some things have changed. The early days of the internet were typified by the fact that its users were also its builders. If you wanted a website in 1994, you had to write your own code. There was no Instagram for your photos, no YouTube for your videos, and no Dropbox for your files. Users built their own websites around their own topics of interest, sometimes tied together in so-called ‘web-rings’, where you could click from one topical site to the next. People were sending each other traffic in the hopes that their users might find more relevant information on other sites, instead of desperately trying to keep users locked into their sites for advertising revenue, as is common practice today. Needing to build your own website, setting up your own webservers, and using non-user friendly applications to transfer data not only meant that most early users had a better core understanding of the technology and what its future might bring, it also meant that users had a sense of ownership. They were shaping the medium they were consuming.
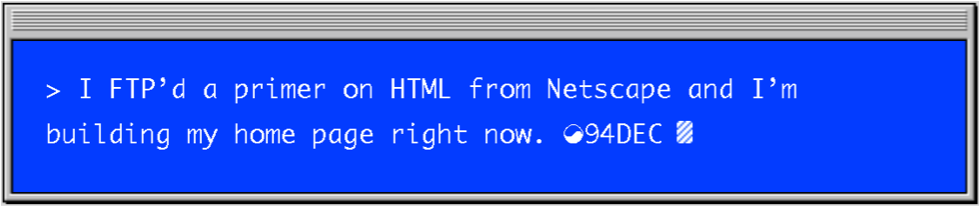
This early internet, a bazaar of small local and exotic offerings made by enthusiasts and hobbyists, no longer exists. It has become a generic shopping mall with the same mega brands across the globe. Where once most users would design and host their websites on a wide range of platforms, most traffic today goes to Facebook, Google and Amazon. But the internet still belongs to no one in particular. With over 3 billion people connected, now more than ever one could argue that the internet belongs to us all. In our daily use and expectancy it functions as a public commons.
Rights regardless of technology
The fact that the internet is used as a public commons, yet is dominated by a handful of mega corporations, makes the following even more urgently in need of examination. What perhaps distinguishes those early debates most from contemporary ones, is that they focused so very little on technology and so much on human rights. Whether or not cryptography should be allowed in form X or form Y is something that detracts from the core issue: should people be allowed to have private conversations? If the answer to that is yes, the answer to whether or not cryptography without backdoors should be legal is simply something that follows. The debates surrounding the forced use of real identities on social media platforms is, in essence, a similar question: should people be allowed to voice opinions anonymously? Again, if the answer to that is yes, the former question has been answered as well.
Shamefully, we now see governments echoing the techno-utopians of yesteryear, proclaiming that regular law does not apply in cyberspace. By somehow declaring freedom of expression, freedom of speech, and freedom of communication to be different in the online realm, governments try to curtail these human rights. Postal mail in the Netherlands, for example, is treated as confidential, but electronic communications are not.
The discussions surrounding new technology will continue long into the future. The mega brands across Silicon Valley are creating ethics boards to deal with questions that arise from new technologies and forms of communication, sometimes giving their own ethics precedence over rights guaranteed by the constitutions they operate in. The only thing stopping a woman in the Netherlands from posting a nipple on Facebook, is Facebook. It’s important to remember that underneath all the jargon, the protocols and bits and bytes, lie questions that are not about technology, but about humanity. These discussions should not be about human rights online but simply about human rights. Just like they were, before you were here.
All images courtesy of WWWTXT, a project curated by Daniel Rehn that collects quotes from old BBS, usenet and other sources of the early days of online networking.
✨This is the fourth in a series of seven commissioned essays for 2019. With these original essays, our aim is to publish work that engages with digital visual culture, both in its niche manifestations and within the technological, political, and mainstream reality of the internet.